Certified Ethical Hacker Practical
Why Choose Us | Certified Ethical Hacker Practical Employment Objective
- Description
- Schedule
- What You'll Learn
- Outline
- Prerequisites
- Income Expectations
- Next Step
- Tuition Fee
- Exam
C|EH Practical is a six-hour, rigorous exam that requires you to demonstrate the application of ethical hacking techniques such as threat vector identification, network scanning, OS detection, vulnerability analysis, system hacking, web app hacking, etc. to solve a security audit challenge.
This is the next step after you have attained the highly acclaimed Certified Ethical Hacker certification.Professionals that possess the C|EH credential will be able to sit for exam that will test them to their limits in unearthing vulnerabilities across major operating systems, databases, and networks.
You will be given limited time, just like in the real world. The exam was developed by a panel of experienced SMEs and includes 20 real-life scenarios with questions designed to validate essential skills required in the ethical hacking domains as outlined in the C|EH program.
It is not a simulated exam but rather, it mimics a real corporate network through the use of live virtual machines, networks, and applications, designed to test your skills. You will be presented with scenarios and will be asked to demonstrate the application of the knowledge acquired in the C|EH course to find solutions to real-life challenges.
The World's First IIT Hacking Industry Readiness Assessment That Is 100% Verified, Online, Live, Proctored!
SCHEDULE DATES - 35 Hour Program
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays)
02/14/2022 02/18/2022
5 Days (35 Hours) a Week for 1 Week
|
||||
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays)
03/07/2022 03/11/2022
5 Days (35 Hours) a Week for 1 Week
|
||||
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays)
Guaranteed to Run (GTR)
04/04/2022 04/08/2022
5 Days (35 Hours) a Week for 1 Week
|
||||
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays)
Guaranteed to Run (GTR)
05/02/2022 05/06/2022
5 Days (35 Hours) a Week for 1 Week
|
||||
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays) |
02/14/2022
02/18/2022 |
5 Days (35 Hours) a Week for 1 Week | ||
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays) |
03/07/2022
03/11/2022 |
5 Days (35 Hours) a Week for 1 Week | ||
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays) |
Guaranteed
to Run (GTR) |
04/04/2022
04/08/2022 |
5 Days (35 Hours) a Week for 1 Week | |
Certified Ethical Hacker (CEH)
9AM - 5PM (Weekdays) |
Guaranteed
to Run (GTR) |
05/02/2022
05/06/2022 |
5 Days (35 Hours) a Week for 1 Week | |
CEH Practical Certification
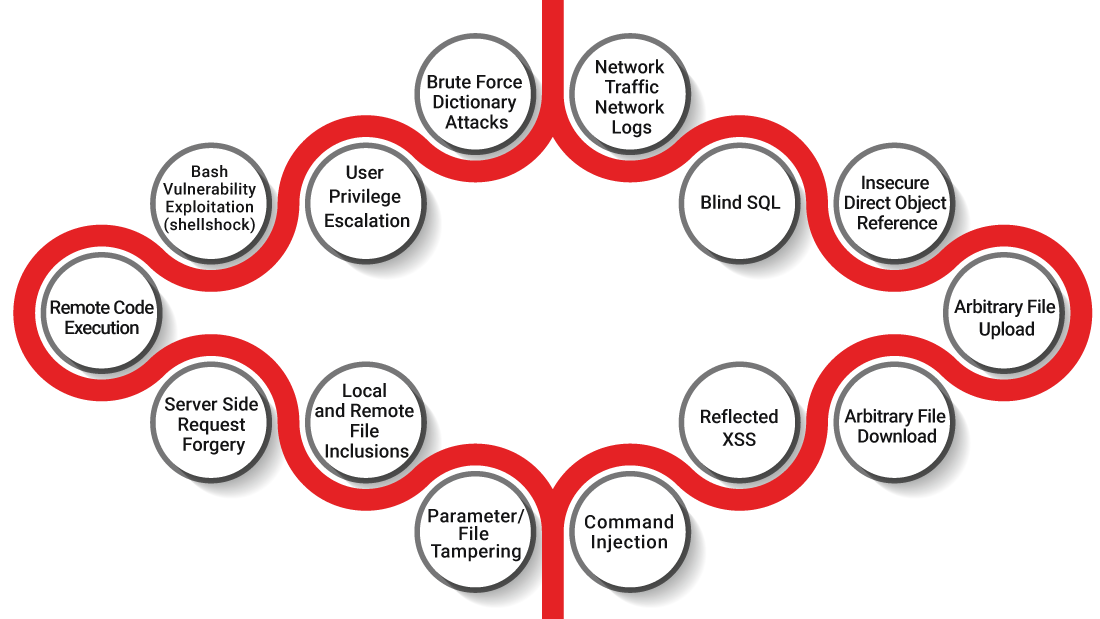
CEH Practical is a 6-hour, rigorous exam that requires you to demonstrate skills and abilities of ethical hacking techniques such as:
- Port scanning tools (e.g., Nmap, Hping)
- Vulnerability detection
- Attacks on a system (e.g., DoS, DDoS, session hijacking, webserver and web application attacks, SQL injection, wireless threats)
- SQL injection methodology and evasion techniques
- Web application security tools (e.g., Acunetix WVS)
- SQL injection detection tools (e.g., IBM Security AppScan)
- Communication protocols
- Port scanning tools (e.g., Nmap, Hping)
- Vulnerability detection
- Attacks on a system (e.g., DoS, DDoS, session hijacking, webserver and web application attacks, SQL injection, wireless threats)
- SQL injection methodology and evasion techniques
- Web application security tools (e.g., Acunetix WVS)
- SQL injection detection tools (e.g., IBM Security AppScan)
- Communication protocols
- Scanning (e.g., Port scanning, banner grabbing, vulnerability scanning, network discovery, proxy chaining, IP spoofing)
- Cryptography
- Cryptography toolkit (e.g., OpenSSL)
- Web server attack methodology
- Operating environments (e.g., Linux, Windows, Mac)
- Web application hacking methodology
- Encryption algorithms
- System hacking (e.g., password cracking, privilege escalation, executing applications, hiding files, covering tracks)
- Vulnerability scanning
- Exploitation tools
- Application/file server
- Database structures
- Wireless and Bluetooth hacking methodology
- Wireless terminologies
- Wireless encryption
- Network/wireless sniffers (e.g., Wireshark, Airsnort)
- Malware (e.g., Trojan, virus, backdoor, worms)
- Botnet
- Malware analysis
- Network sniffing
- Backups and archiving (e.g., local, network)
- Data analysis
- Log analysis tools
- Cryptanalysis tool (e.g., CrypTool)
This is the next step to become a CEH Master after you have achieved your CEH certification. Within CEH Practical, you have a limited amount of time to complete 20 challenges testing your skills and proficiency in a performance-based cyber range. This exam is NOT a simulation and incorporates a live corporate network of VMs and applications with solutions to uncover vulnerabilities.
C|EH Certified Ethical Hacker Practical Training Courses
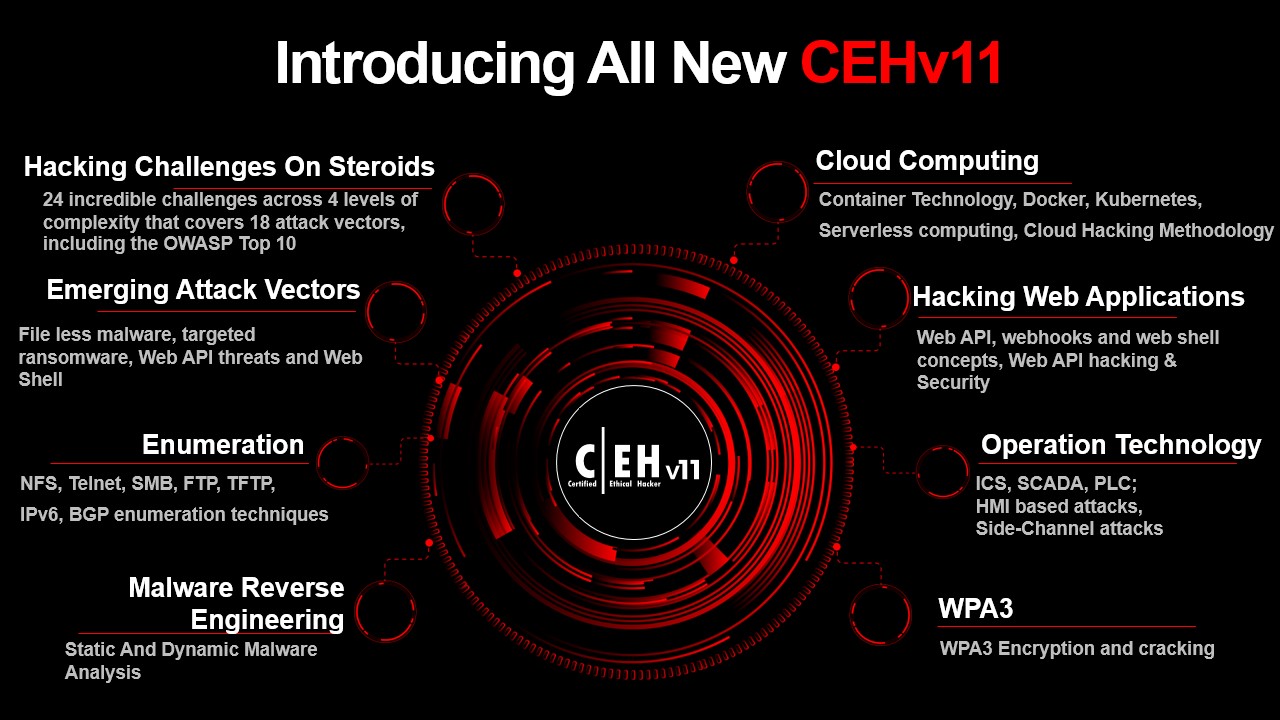
Module 01: Introduction to Ethical Hacking
Module 02: Footprinting and Reconnaissance
Module 03: Scanning Networks
Module 04: Enumeration
Module 05: Vulnerability Analysis
Module 06: System Hacking
Module 07: Malware Threats
Module 08: Sniffing
Module 09: Social Engineering
Module 10: Denial-of-Service
Module 11: Session Hijacking
Module 12: Evading IDS, Firewalls, and Honeypots
Module 13: Hacking Web Servers
Module 14: Hacking Web Applications
Module 15: SQL Injection
Module 16: Hacking Wireless Networks
Module 17: Hacking Mobile Platforms
Module 18: IoT Hacking
Module 19: Cloud Computing
Module 20: Cryptography
The preparatory course for this certification is the Certified Ethical Hacker course. While there is no additional course or training required, we strongly recommend that you attempt the C|EH (Practical) exam only if you have attended the current C|EH course/equivalent. The aim of this credential is to help set gifted ethical hacking practitioners apart from the crowd.
Certified Ethical Hacker Practical
Eligibility Criteria
- Be a C|EH (any version) member in good standing (Your USD 100 application fee will be waived);
- or Have a minimum of 3 years working experience in InfoSec domain (You will need to pay USD 100 as a non-refundable application fee)
- or Have any other industry equivalent certifications such as OSCP or GPEN cert (You will need to pay USD 100 as a non-refundable application fee).
- HS Diploma/GED
Income Expectation
$111,200/yr
The average salary for a Ethical Hacker Practical Certified Employee is $111,200 in New York City. Salary estimates are provided by Cybersecurity .
Certified Ethical Hacker Practical Objective
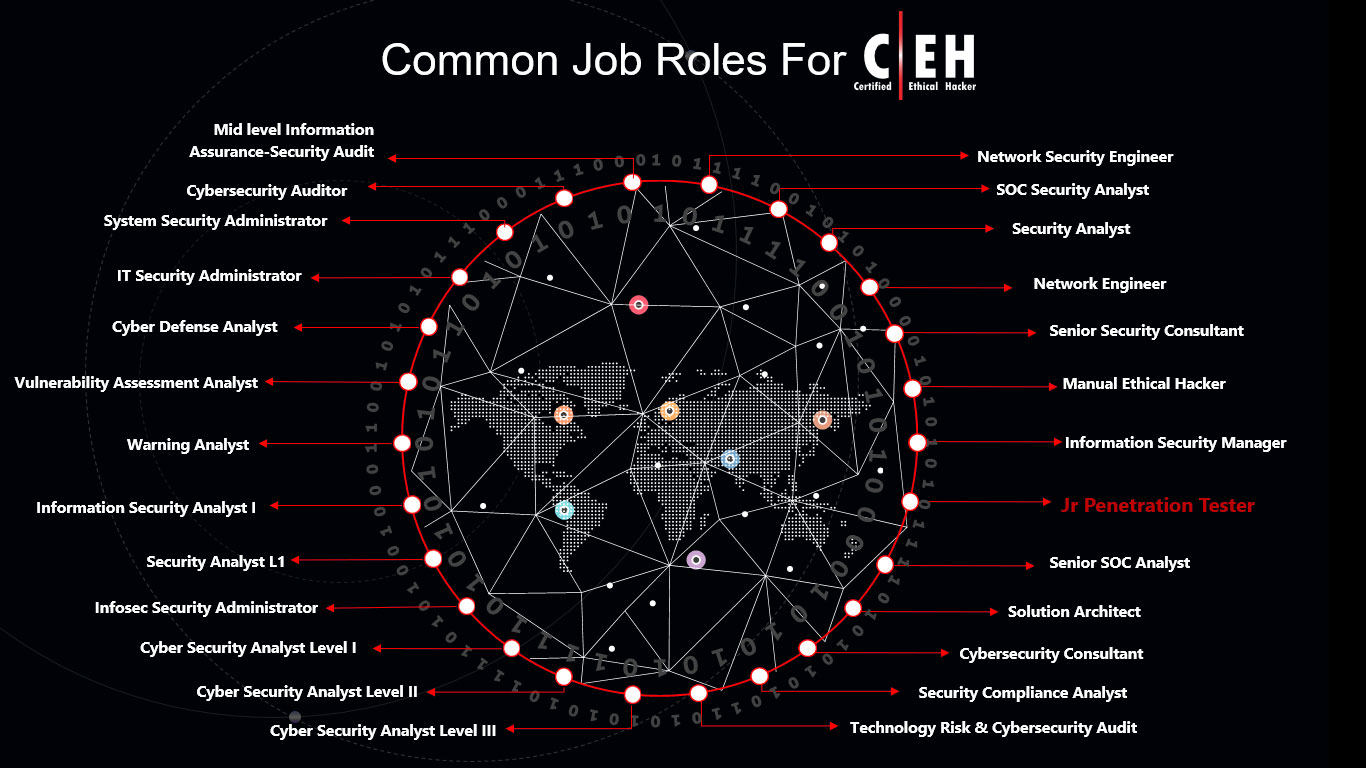
Upon completion of this course, and the certifying exam(s), the student will be qualified to take a job as a
Ethical Hacker
IT Security Specialist
Network Security Specialist
Security Administrator.
or IT Security Consultant.
Certified Network Defender Certification C|ND
Licensed Penetration Tester Master L |PT
EC Council Certified Security Licensed Penetration Tester | ECSA
Computer Hacking Forensic Investigator
$3,000.00
Exam
About the Exam
- Exam Title: Certified Ethical Hacker (Practical)
- Number of Questions: 125
- Test Duration: 4 Hours
- Test Format: Multiple Choice
- Test Delivery: ECC EXAM, VUE
- Exam Prefix: 312-50 (ECC EXAM), 312-50 (VUE)
Passing Score:
In order to maintain the high integrity of our certification exams, EC-Council Exams are provided in multiple forms (I.e. different question banks). Each form is carefully analyzed through beta testing with an appropriate sample group under the purview of a committee of subject matter experts that ensure that each of our exams not only has academic rigor but also has real world applicability. We also have a process to determine the difficulty rating of each question. The individual rating then contributes to an overall cut score for each exam form. To ensure each form has equal assessment standards, cut scores are set on a “per exam form” basis. Depending on which exam form is challenged, cut scores can range from 60% to 85%.
How to Schedule the C|EH (Practical) Exam
Application Process
- Applicants can apply via the online web form Click here to attempt the certification or purchase an exam voucher from one of our many globally accredited training partners.
- Important Information for Applicants: On an average, an application processing time would be between 5-10 working days once the verifiers on the application respond to IIT’s requests for information.
- On the application, there is a section for the applicant to list their previous manager, supervisor, or department lead who will act as their verifier. Please note that Institute of Information Technology reaches out to the listed verifier to confirm the applicant's experience. By making the application, you provide consent to Institute of Information Technology to contact your chosen verifier.
- After the application is submitted, should the certification team require further information, the applicant shall have up to 90 days to provide such information. After that period, should there be no response from the applicant, the application will be automatically rejected and a new form will have to be submitted.
- If the application is approved, the applicant will be sent instructions on purchasing the exam kit which cost $550 from IIT directly.
- If application is not approved, the application fee of USD 100 will not be refunded.
- The approved application is valid for 3 months from the date of approval so the candidate must purchase the official kit within 3 months. After the kit is released, the applicant has 3 months to utilize the codes.
- Should you require the exam voucher validity to be extended, kindly contact admissions@iitlearning.com before the expiry date. Only valid/ active codes can be extended.
- An application extension request shall be at the discretion of the Director of Certification
Exam Sanctity
The trust that the industry places in our credentials is very important to us. We see it as our duty to ensure that the holders of this credential are proven hands-on, ethical hackers who are able to perform in the real world to solve real world challenges.
As such, the C|EH| Practical is designed as a hands-on exam that will test the skills of the ethical hacker BEYOND just their knowledge.
This exam is a proctored, practical exam that can last up to 6 hours.
We know that travelling to an exam center can be difficult for many. We are pleased to announce that you can take the C|EH (Practical) exam from the comfort of your home, but you need to be prepared to be proctored by a dedicated Institute of Information Technology Proctor certification team under strict supervision.